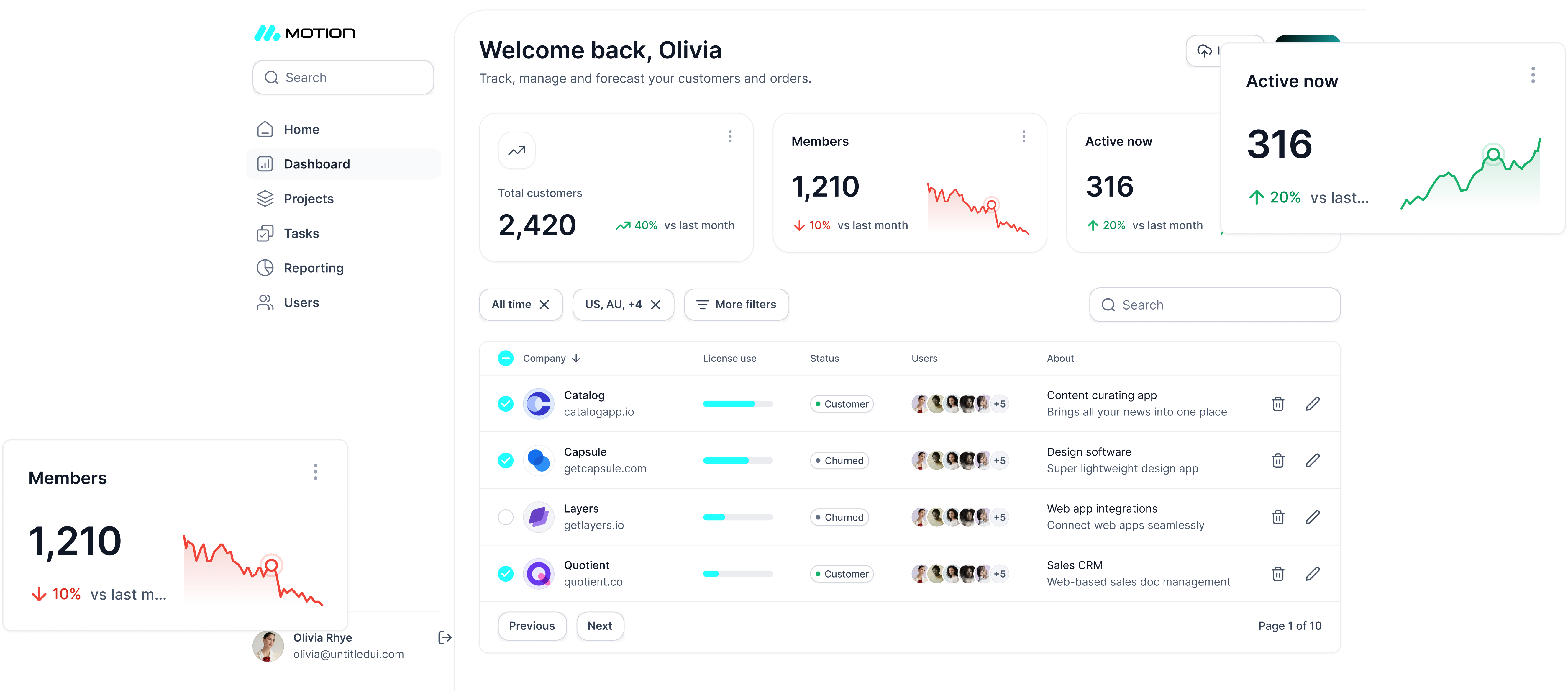
Streamline Your Logisitics with Motion
Motion is an on-demand delivery platform that connects shippers with efficient transportation solutions—whether by road, air, or sea. Our intuitive system empowers businesses to manage and track shipments in real time, ensuring a seamless and transparent delivery experience.